Saturday, March 17, 2012
Willy Wonka Remix – You Get Nothing [Video]
Willy Wonka Remix – You Get Nothing [Video]:

Today I tripped over this very cool remix of a scene from Willy Wonka and the Chocolate Factory that will forever be my soundtrack piece in the back of my head if I ever deny someone something.
Check out “You Get Nothing” with Gene Wilder as Willy Wonka and Featuring Grandpa Jo (unaccredited shocked looks from Charlie included)
Now just about anyone with Windows Movie Maker and a bittorrent client can mash together a remix, but this is very well done and all kinds of entertaining. (Like the Unexpected Game Boy Music Video we saw earlier)
I’d put this on my iPod!
Via
No related posts.



Today I tripped over this very cool remix of a scene from Willy Wonka and the Chocolate Factory that will forever be my soundtrack piece in the back of my head if I ever deny someone something.
Check out “You Get Nothing” with Gene Wilder as Willy Wonka and Featuring Grandpa Jo (unaccredited shocked looks from Charlie included)
Now just about anyone with Windows Movie Maker and a bittorrent client can mash together a remix, but this is very well done and all kinds of entertaining. (Like the Unexpected Game Boy Music Video we saw earlier)
I’d put this on my iPod!
Via
No related posts.

Friday, March 16, 2012
World earthquakes 2011 Visualization map
World earthquakes 2011 Visualization map:
All earthquakes of 2011 displayed on the globe in a video that represents depth and intensity for ea..(Read...)

All earthquakes of 2011 displayed on the globe in a video that represents depth and intensity for ea..(Read...)
I made a single panel Garfield minus Garfield (Via me).
I made a single panel Garfield minus Garfield (Via me).: 
I made a single panel Garfield minus Garfield (Via me).

I made a single panel Garfield minus Garfield (Via me).
03/14/12 PHD comic: 'Staring contest'
03/14/12 PHD comic: 'Staring contest':
| Piled Higher & Deeper by Jorge Cham | www.phdcomics.com | |
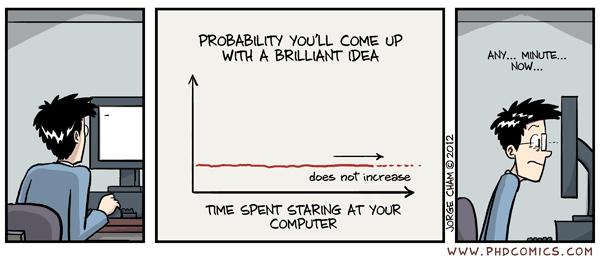 | ||
title: "Staring contest" - originally published 3/14/2012 For the latest news in PHD Comics, CLICK HERE! | ||
Thursday, March 15, 2012
Wednesday, March 14, 2012
New study: Passwords are still the weakest link
New study: Passwords are still the weakest link:  The latest review of security issues and trends is out, and we're sorry to say, folks: The rampant use of weak passwords still presents a serious security problem to end users and companies alike.
The latest review of security issues and trends is out, and we're sorry to say, folks: The rampant use of weak passwords still presents a serious security problem to end users and companies alike.
The recently-published Trustwave 2012 Global Security Report details the current threats to user data and identifies the vulnerabilities that persist within organizations. The statistics were generated from their investigation of about 300 breaches across 18 countries. They also analyzed the usage and weakness trends of more than 2 million real-world passwords used within corporate information systems. The verdict? After an initial foothold in a system (via malware and other threat vectors), 80% of security incidents were due to the use of weak administrative passwords.
Yes, that's correct: 80 percent. From weak passwords.
"The use of weak and/or default credentials continues to be one of the primary weaknesses exploited by attackers for internal propagation," the report comments. "This is true for both large and small organizations, and largely due to poor administration."
They found that writing down passwords is still prevalent in the workplace, particularly in organizations that implement complexity requirements, password expiration cycles, and password histories to prevent recycling of old passwords. While these policies are often implemented to improve password management, the reality is that increasing password complexity directly corresponds with a decrease in memorability, hence the insecure practice of writing down passwords. The report found that in 15% of the security tests performed, written passwords were found on or around user work stations.
What's even more astonishing is that rather than find a tool that can help with the password problem, users are getting creative in overriding the policies meant to enforce the use of strong passwords. They exploit loopholes such as:
In another alarming example, the report highlights Active Directory's policy of password complexity, which states that a password is required to have a minimum of eight characters and three of the five character types (Lower Case, Upper Case, Numbers, Special, Unicode). Guess what meets those requirements? "Password1", "Password2", and "Password3", the first being the most widely used across the pool of two million passwords studied in the report.
The top 10 passwords identified by the study were:
Other keywords included:
In some ways, we're impressed by the creative effort people put into avoiding strong passwords while still operating within the "complexity requirements" imposed on them.
However, moving forward into 2012 and beyond, it's clear there are steps both end users and businesses should be taking to change their password habits, prioritizing:
Best,
The LastPass Team

 The latest review of security issues and trends is out, and we're sorry to say, folks: The rampant use of weak passwords still presents a serious security problem to end users and companies alike.
The latest review of security issues and trends is out, and we're sorry to say, folks: The rampant use of weak passwords still presents a serious security problem to end users and companies alike.The recently-published Trustwave 2012 Global Security Report details the current threats to user data and identifies the vulnerabilities that persist within organizations. The statistics were generated from their investigation of about 300 breaches across 18 countries. They also analyzed the usage and weakness trends of more than 2 million real-world passwords used within corporate information systems. The verdict? After an initial foothold in a system (via malware and other threat vectors), 80% of security incidents were due to the use of weak administrative passwords.
Yes, that's correct: 80 percent. From weak passwords.
"The use of weak and/or default credentials continues to be one of the primary weaknesses exploited by attackers for internal propagation," the report comments. "This is true for both large and small organizations, and largely due to poor administration."
They found that writing down passwords is still prevalent in the workplace, particularly in organizations that implement complexity requirements, password expiration cycles, and password histories to prevent recycling of old passwords. While these policies are often implemented to improve password management, the reality is that increasing password complexity directly corresponds with a decrease in memorability, hence the insecure practice of writing down passwords. The report found that in 15% of the security tests performed, written passwords were found on or around user work stations.
What's even more astonishing is that rather than find a tool that can help with the password problem, users are getting creative in overriding the policies meant to enforce the use of strong passwords. They exploit loopholes such as:
- Setting usernames as the password when complexity requirements aren't forced
- Adding simple variations to fit complexity requirements, such as capitalizing a letter and adding an exclamation point to the end
- Using dictionary words or applying simple modifications
In another alarming example, the report highlights Active Directory's policy of password complexity, which states that a password is required to have a minimum of eight characters and three of the five character types (Lower Case, Upper Case, Numbers, Special, Unicode). Guess what meets those requirements? "Password1", "Password2", and "Password3", the first being the most widely used across the pool of two million passwords studied in the report.
The top 10 passwords identified by the study were:
- Password1
- welcome
- password
- Welcome1
- welcome1
- Password2
- 123456
- Password01
- Password3
- P@ssw0rd
Other keywords included:

In some ways, we're impressed by the creative effort people put into avoiding strong passwords while still operating within the "complexity requirements" imposed on them.
However, moving forward into 2012 and beyond, it's clear there are steps both end users and businesses should be taking to change their password habits, prioritizing:
- Education of employees on basic security practices
- Tracking of company data and pinning it to an individual every time
- Standardizing implementation across all platforms and devices
- The implementation of a password management tool that makes it easy to maintain high security standards.
Best,
The LastPass Team
Tuesday, March 13, 2012
Evidence of Lost Da Vinci Fresco Behind Florentine Wall
Evidence of Lost Da Vinci Fresco Behind Florentine Wall:
Lev13than writes "Art historians working in Florence's city hall claim to have found evidence of Leonardo da Vinci's lost Battle of Anghiari fresco. Painted in 1505, the fresco was covered over by a larger mural during mid-16th Century palace renovations. Historians have long speculated that the original work was protected behind a false wall. Attempts to reveal the truth have been complicated by the need to protect Vasari's masterpiece Battle of Marciano that now graces the room. By drilling small holes into previously-restored sections of Vasari's fresco, researchers used endoscopic cameras and probes to determine that a second wall does exist. They further claim that the hidden wall is adorned with pigments consistent with Leonardo's style. The research has set off a storm of controversy between those who want to find the lost work and others who believe that it is gone, and that further exploration risks destroying the existing artwork."
Read more of this story at Slashdot.

Lev13than writes "Art historians working in Florence's city hall claim to have found evidence of Leonardo da Vinci's lost Battle of Anghiari fresco. Painted in 1505, the fresco was covered over by a larger mural during mid-16th Century palace renovations. Historians have long speculated that the original work was protected behind a false wall. Attempts to reveal the truth have been complicated by the need to protect Vasari's masterpiece Battle of Marciano that now graces the room. By drilling small holes into previously-restored sections of Vasari's fresco, researchers used endoscopic cameras and probes to determine that a second wall does exist. They further claim that the hidden wall is adorned with pigments consistent with Leonardo's style. The research has set off a storm of controversy between those who want to find the lost work and others who believe that it is gone, and that further exploration risks destroying the existing artwork."
Read more of this story at Slashdot.
The Quest For Perfect Mashed Potatoes
The Quest For Perfect Mashed Potatoes:

I recently attended a wonderful wine tasting called the Seattle Food and Wine Experience. This annual event features producers from Washington, Oregon and California, along with brewers and hand-crafted distillers.
The dazzling lineup is complemented by impressive food from some of the regions' best chefs, who create dishes designed to pair with wine. One of the most memorable bites I tried was from the mashed potato bar, a lineup of several types of spuds simply smashed and topped with various savories.
I absolutely love mashed potatoes. It was a big bummer when that trend faded away, making way for all manner of mac-and-cheese. But I make them often at home, especially with St. Patrick's Day on the horizon. Can't fight the Irish in my family tree.
I've tried various approaches, cranking them through ricers, using old-fashioned mashers, even pulsing them in the food processor. But nothing works quite as well as my trusty hand mixer. The trick is not to over-whip or they turn glue-y. I don't mind a few lumps.
And when it comes to the liquid to mash them with? I've tried cream and buttermilk. Olive oil and stock work just fine. But whole milk seems to lead to the fluffiest mashed potatoes. And if they're seasoned just right, with a generous pinch or two of sea salt, then all I really need to complete this picture of happiness is a little butter on top.
-- Leslie Kelly
I recently attended a wonderful wine tasting called the Seattle Food and Wine Experience. This annual event features producers from Washington, Oregon and California, along with brewers and hand-crafted distillers.
The dazzling lineup is complemented by impressive food from some of the regions' best chefs, who create dishes designed to pair with wine. One of the most memorable bites I tried was from the mashed potato bar, a lineup of several types of spuds simply smashed and topped with various savories.
I absolutely love mashed potatoes. It was a big bummer when that trend faded away, making way for all manner of mac-and-cheese. But I make them often at home, especially with St. Patrick's Day on the horizon. Can't fight the Irish in my family tree.
I've tried various approaches, cranking them through ricers, using old-fashioned mashers, even pulsing them in the food processor. But nothing works quite as well as my trusty hand mixer. The trick is not to over-whip or they turn glue-y. I don't mind a few lumps.
And when it comes to the liquid to mash them with? I've tried cream and buttermilk. Olive oil and stock work just fine. But whole milk seems to lead to the fluffiest mashed potatoes. And if they're seasoned just right, with a generous pinch or two of sea salt, then all I really need to complete this picture of happiness is a little butter on top.
-- Leslie Kelly
Monday, March 12, 2012
Time — With Robert the Plant!
Time — With Robert the Plant!:

It’s the very best of Robert the Plant!!
As I’m working on my mysterious graphic novel this week(more details soon!), please enjoy the craziness that is Robert! New strips return next week!
Thanks, friends!
-Lucas
Don’t forget the new book “Toys in the Attic” is now for sale! Head on over to the store and get your copy of either the Artist Edition, or the Regular Edition, today!




It’s the very best of Robert the Plant!!
As I’m working on my mysterious graphic novel this week(more details soon!), please enjoy the craziness that is Robert! New strips return next week!
Thanks, friends!
-Lucas
Don’t forget the new book “Toys in the Attic” is now for sale! Head on over to the store and get your copy of either the Artist Edition, or the Regular Edition, today!


Sunday, March 11, 2012
Subscribe to:
Comments (Atom)


